Insider data theft and malware attacks top the list of the most significant concerns for enterprise security executives, a new report from Accenture and HfS Research reveals. Of those surveyed, a majority (69 percent) of respondents experienced an attempted or successful theft or corruption of data by insiders during the prior 12 months, with media and technology organizations reporting the highest rate (77 percent).
This insider risk will continue to be an issue, with security professionals' concerns over insider theft of corporate information alone rising by nearly two-thirds over the coming 12 to 18 months. Additionally, the research shows that a budget shortage for hiring cyber-security talent and well-trained employees is hindering the ability of organizations to properly defend themselves against these attacks.
The survey, ""The State of Cybersecurity and Digital Trust 2016'"", was conducted by HfS Research on behalf of Accenture. More than 200 C-level security executives and other IT professionals were polled across a range of geographies and vertical industry sectors. The survey examined the current and future state of cyber-security within the enterprise and the recommended steps to enable digital trust throughout the extended ecosystem. The findings indicate that there are significant gaps between talent supply and demand, a disconnect between security teams and management expectations, and considerable disparity between budget needs and actual budget realities.
""Our research paints a sobering picture. Security leaders believe threats are not going away, in fact they expect them to increase and hinder their ability to safeguard critical data and establish digital trust,"" said Kelly Bissell, senior managing director, Accenture Security. ""At the same time, while organizations want to invest in advanced cyber technologies, they simply don't have enough budget to recruit or train skilled people to use that technology effectively. To better manage this security problem, businesses will need to work in tandem with the extended enterprise ecosystem - business units, partners, providers and end users - to create an environment of digital trust.""
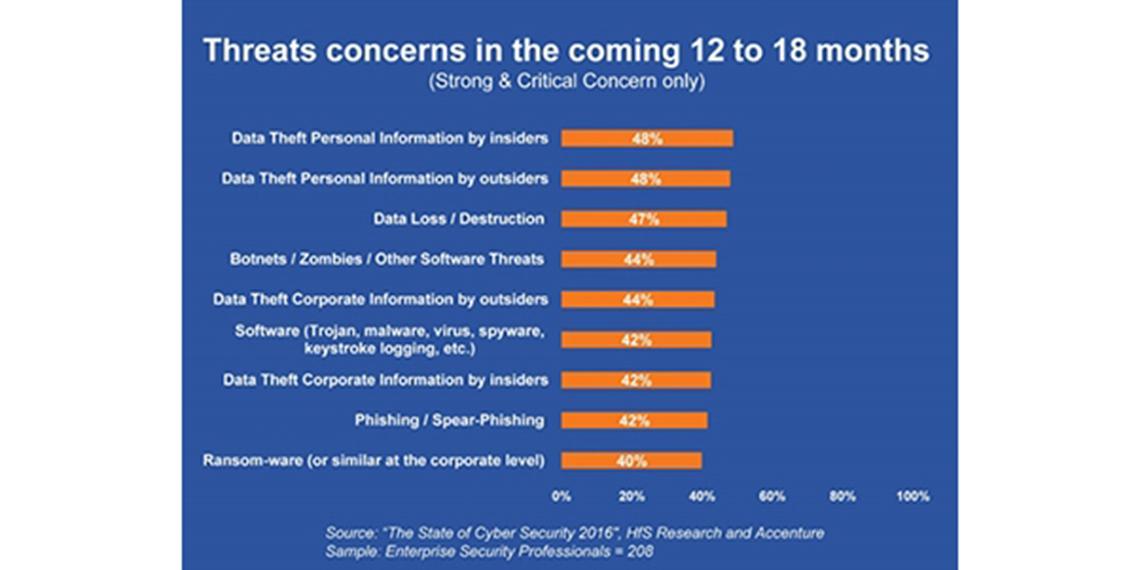
Despite having advanced technology solutions, nearly half of all respondents (48 percent) indicate they are either strongly or critically concerned about insider data theft and malware infections (42 percent) in the next 12 to 18 months. When asked about current funding and staffing levels some 42 percent of respondents said they need more budget for hiring cyber-security professionals and for training. More than half (54 percent) of respondents also indicated that their current employees are underprepared to prevent security breaches and the numbers are only slightly better when it comes to detecting (47 percent) and responding (45 percent) to incidents.
The report identified five significant gaps disrupting the ability of enterprises to effectively prevent or mitigate well-organized and targeted cyber attacks, including:
- Talent: Thirty-one percent list either lack of training or staffing budget as their single biggest inhibitor to combating attacks.
- Technology: Firewalls and encryption top the list of the most important technologies to combat cyber threats, but the largest increase in deployments anticipated in the next 12 to 18 months are in the areas of cognitive computing and AI (31 percent) and data anonymization (25).
- Parity: An enterprise is only as secure as its least secure partner, yet only 35-57 percent of all enterprises said they assess ecosystem partners for cyber integrity and preparedness, with BPO partners being the least vetted and credit partners being the most vetted.
- Budget: Seventy percent cite a lack of, or inadequate, funding for either cybersecurity technology or security talent, including training.
- Management: While 54 percent of respondents agree or strongly agree that cybersecurity is an enabler of digital trust for consumers, 36 percent believe that their executive management considers cybersecurity an unnecessary cost.
""While the gaps we identified can be overcome, they do collectively underscore the need for an inherently different approach, one that includes more robust risk management measures and the development of digital trust,"" said Fred McClimans, research vice president, Digital Trust and Cybersecurity, HfS Research. ""There is an important opportunity to address these gaps by rethinking how digital trust and security can be holistically woven into the enterprise fabric through the integration of automation and AI solutions as well as through business partnerships and processes.""